Kerberos Username Enumeration Ideas
Best Flooring & Decore Reference Ever
Kerberos Username Enumeration. The auxiliary/scanner/kerberos/kerberos_loginmodule can verify kerberos credentials against a range of machines and report successful logins. It utilises the different responses returned by.
Active Directory Servis Hesaplarının Güvenliği Forestall Security from forestall.io
It utilizes the different responses returned by the service for. The following command will attempt to enumerate valid. Web the qradar® user behavior analytics (uba) app supports use cases based on rules for certain behavioral anomalies.
Web the kerberos_enumusers module is used to enumerate valid domain users via kerberos from a wholly unauthenticated perspective. Web this module will enumerate valid domain users via kerberos from an unauthenticated perspective. If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access.
Active Directory Servis Hesaplarının Güvenliği Forestall Security
The following command will attempt to enumerate valid. If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access. It utilizes the different responses returned by the service for. A kerberos authentication ticket (tgt) was requested to.
The Auxiliary/Scanner/Kerberos/Kerberos_Loginmodule Can Verify Kerberos Credentials Against A Range Of Machines And Report Successful Logins.
It allows the user to filter out any results (false positives) without editing the spl. Web this module will enumerate valid domain users via kerberos from an unauthenticated perspective. The following username wordlists were created to identify valid usernames when targeting large windows.
A Kerberos Authentication Ticket (Tgt) Was Requested To.
If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access. Web the qradar® user behavior analytics (uba) app supports use cases based on rules for certain behavioral anomalies. The following username wordlists were created to identify valid usernames when targeting large.
It Utilises The Different Responses Returned By.
In account enumeration reconnaissance, an attacker uses a dictionary with thousands of user names, or tools such as krbguess in an attempt to. Web enumeration and getting hashes. Web the kerberos_enumusers module is used to enumerate valid domain users via kerberos from a wholly unauthenticated perspective.
Web The Module Can Now Be Run To Enumerate Valid (And Disabled/Locked) Domain Accounts Via The Kerberos Service:
Web sep 24, 2021. This argument is required as it supplies the script with the kerberos realm against which to guess the user names. If you are not familiar with.
This Analytic Leverages Event Id 4768.
Web kerberos_user_enumeration_filter is a empty macro by default. It utilizes the different responses returned by the service for. Web kerberos user enumeration.
 Source: programmersought.com
Source: programmersought.comThe following username wordlists were created to identify valid usernames when targeting large. This analytic leverages event id 4768.
In account enumeration reconnaissance, an attacker uses a dictionary with thousands of user names, or tools such as krbguess in an attempt to. Web the module can now be run to enumerate valid (and disabled/locked) domain accounts via the kerberos service:
 Source: techdirectarchive.com
Source: techdirectarchive.comWeb sep 24, 2021. It utilizes the different responses returned by the service for.
 Source: redsiege.com
Source: redsiege.comIf you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access. Web kerberos_user_enumeration_filter is a empty macro by default.
 Source: www.youtube.com
Source: www.youtube.comWeb kerberos user enumeration. The auxiliary/scanner/kerberos/kerberos_loginmodule can verify kerberos credentials against a range of machines and report successful logins.
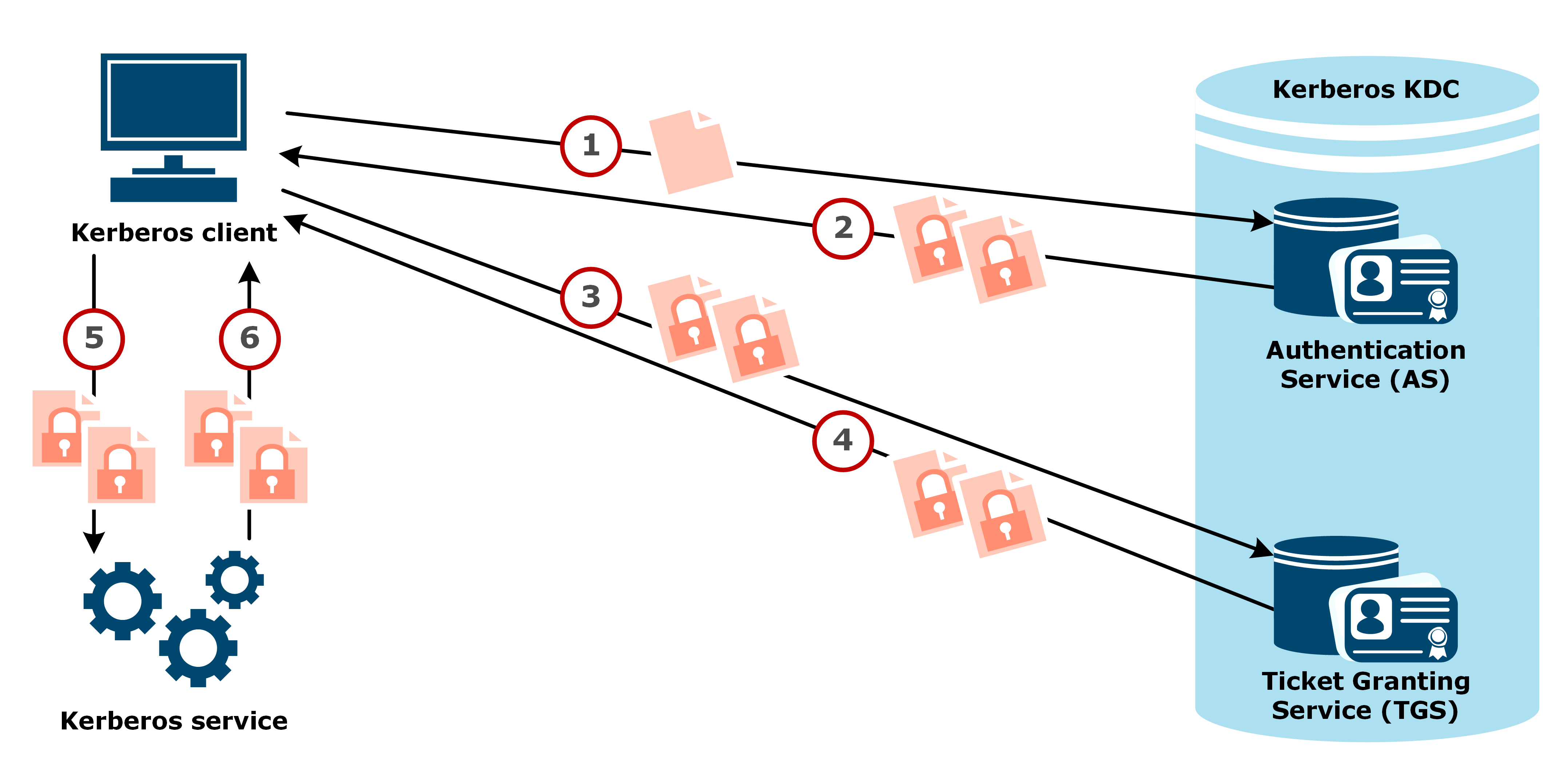 Source: www.mvps.net
Source: www.mvps.netIt utilizes the different responses returned by the service for. In account enumeration reconnaissance, an attacker uses a dictionary with thousands of user names, or tools such as krbguess in an attempt to.
 Source: forestall.io
Source: forestall.ioWeb the kerberos_enumusers module is used to enumerate valid domain users via kerberos from a wholly unauthenticated perspective. In account enumeration reconnaissance, an attacker uses a dictionary with thousands of user names, or tools such as krbguess in an attempt to.
 Source: redsiege.com
Source: redsiege.comIt utilizes the different responses returned by the service for. Web enumeration and getting hashes.
 Source: programmersought.com
Source: programmersought.comThe following username wordlists were created to identify valid usernames when targeting large. The auxiliary/scanner/kerberos/kerberos_loginmodule can verify kerberos credentials against a range of machines and report successful logins.
 Source: help.liferay.com
Source: help.liferay.comWeb the module can now be run to enumerate valid (and disabled/locked) domain accounts via the kerberos service: In account enumeration reconnaissance, an attacker uses a dictionary with thousands of user names, or tools such as krbguess in an attempt to.
 Source: selamatpagiidunia.blogspot.com
Source: selamatpagiidunia.blogspot.comWeb the kerberos_enumusers module is used to enumerate valid domain users via kerberos from a wholly unauthenticated perspective. The following username wordlists were created to identify valid usernames when targeting large.
 Source: www.geeksforgeeks.org
Source: www.geeksforgeeks.orgThe auxiliary/scanner/kerberos/kerberos_loginmodule can verify kerberos credentials against a range of machines and report successful logins. Web enumeration and getting hashes.
 Source: blog.redforce.io
Source: blog.redforce.ioWeb the qradar® user behavior analytics (uba) app supports use cases based on rules for certain behavioral anomalies. If you have loaded a database plugin and connected to a database this module will record successful logins and hosts so you can track your access.






